使用方法
- 安装
certbot
参考使用certbot+nginx搭建https服务器 - 使用
certbot获取ssl证书# 其中*.eoekun.top为泛域名 sudo ./certbot-auto --server https://acme-v02.api.letsencrypt.org/directory -d *.eoekun.top -d eoekun.top --manual --preferred-challenges dns-01 certonly - 详细过程
# 根据提示进行相应的交互 # 根据提示在域名解析服务商上添加TXT解析 Please deploy a DNS TXT record under the name _acme-challenge.eoekun.top with the following value: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX Before continuing, verify the record is deployed. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Press Enter to Continue - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Please deploy a DNS TXT record under the name _acme-challenge.eoekun.top with the following value: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX Before continuing, verify the record is deployed. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - # 验证通过 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Press Enter to Continue Waiting for verification... Cleaning up challenges IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/eoekun.top-0001/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/eoekun.top-0001/privkey.pem Your cert will expire on 2018-12-03. To obtain a new or tweaked version of this certificate in the future, simply run certbot-auto again. To non-interactively renew *all* of your certificates, run "certbot-auto renew" - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le最后的一段
Congratulations中有说明公钥私钥存储位置,将用于下面的nginx配置 nginx配置证书server { if ($host = eoekun.top) { return 301 https://$host$request_uri; } # managed by Certbot listen 80; server_name eoekun.top; return 404; # managed by Certbot } server { server_name eoekun.top; access_log logs/eoekun.access.log main; location / { if (!-e $request_filename){ rewrite ^(.*)$ /$1.html last; break; } root /data/blog/jekyll; index index.html; } listen 443 ssl; # managed by Certbot ssl_certificate /etc/letsencrypt/live/eoekun.top-0001/fullchain.pem; # managed by Certbot ssl_certificate_key /etc/letsencrypt/live/eoekun.top-0001/privkey.pem; # managed by Certbot include /etc/letsencrypt/options-ssl-nginx.conf; # managed by Certbot ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem; # managed by Certbot }主要添加一个
80端口的301跳转,然后配置443的证书路径即可
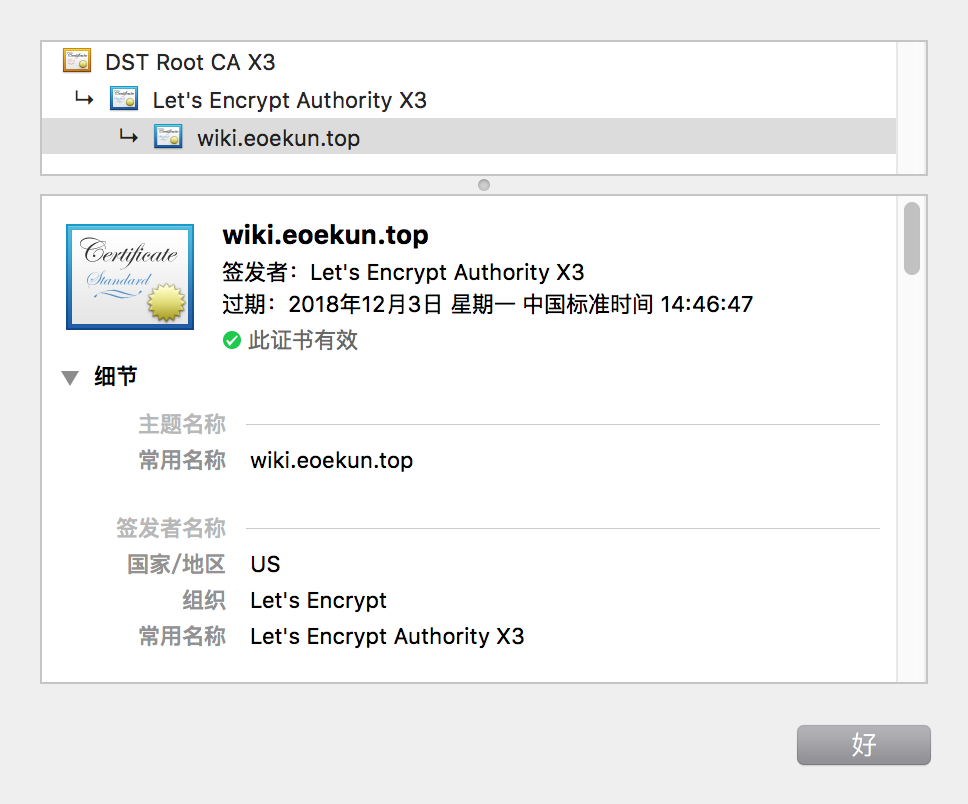
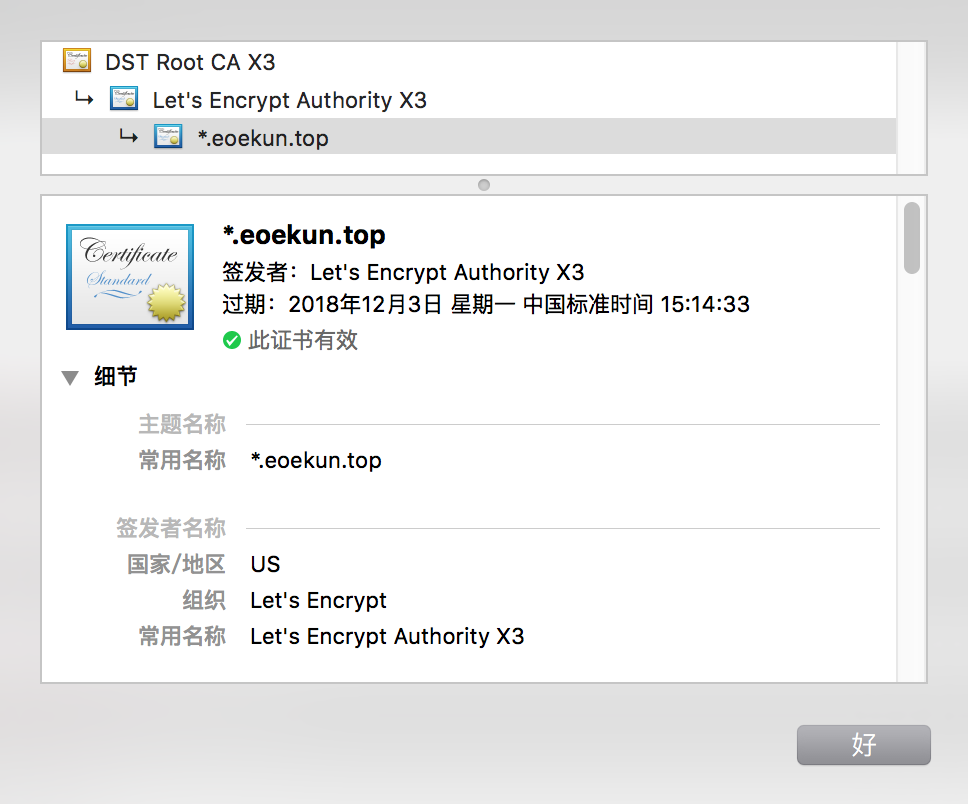
普通域名证书与泛域名证书对比
- 二级域名证书
wiki.eoekun.top - 泛域名证书
*.eoekun.top